My Home
If you own a cell phone, you're likely familiar with the 9-dot grid security pattern. One may think that there is a large number of possible patters, with a maximum of
.
This is due to constraint 1:
Constraint 1. Each dot can only be used once.
This seems reasonably secure: this seems to be about the same number of patterns as there are four-letter password using only the characters on the default keyboard (a through z):
.
We will see later that this is false, due to another constraint, but right now we will consider: should we allow ourselves to one of all possible patterns (including those that may contain only one, two or three dots)?
There are two conflicting constraints:
- If you use only a 9-dot pattern, then you are severely reducing
the search space (all possible patterns you need to try) that someone trying to hack your phone has to try:
, while
- If your particular pattern is too short (say five dots), then there are other means of easily seeing your password (say, by someone looking over your shoulder).
Thus, I would recommend that vary the number of dots in your pattern within reason. I would recommend between 7 and 9 dots. If you change your pattern often, choose the number of dots as follows:
- Keep rolling a six-sided die until you get a 1 through 5.
- If it is a 1 or a 2, use 9 dots,
- if it is a 3 or 4, use 8 dots, and
- If it is a 5, us seven dots.
This will make it difficult for someone to guess your pattern, because he or she will have to try all 7-, 8- and 9-dot patterns, and the total number of possible patterns appears to be around 907200—pretty close to the total number of possible patterns.
Now, there is one further constraint that severely limits the number of possible patterns.
Constraint 2. You cannot skip dots in a straight line if you have not already visited them.
I will explain this as follows: I will number the dots as shown in Figure 1.
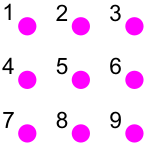
Figure 1. Numbering the dots.
For example, if you start with dot 1, you cannot have a pattern such as 1-3 1-7 or 1-9: if you try to, the program will add the intermediate number automatically: 1-2-3, 1-4-7 and 1-5-9, respectively. You can, however, skip over dots if you have already visited them; for example, 2-5-1-3 is allowed.
If you count all possible patterns now, we have:
- 106369 possible patterns if we consider all possible dots, and
- 71628 possible patterns if we restrict ourselves to patterns with 7, 8 or 9 dots.
Okay, so , so it can still be
slightly more secure than a three-letter password.
There is one final constraint:
Constraint 3. Your finger cannot leave the touch pad.
This final constraint is already factored into what we discussed above, but the consequence is that you can see the smudges on the screen. Therefore, it is really easy to deduce the pattern by looking at the smudges. For example, the smudge in Figure 2 is either from 7-4-2-1-5-3-6-9 or 9-6-3-5-1-2-4-7.

Figure 2. A smudge read from the screen.
To prevent your pattern from being read, you may continue tracing a pattern on the screen so long as you don't let go and don't come near any of the dots that you have not yet visited. To correct the situation in Figure 3, suppose we ended at 9, in this case, go back to 1, across to 3 and then to 7. This will leave the smudge pattern in Figure 3. I call this a victory lap because you've finished the pattern—this is just added dressing.

Figure 3. Three more dots forming a victory lap
Notice from the smudge that you cannot tell where the pattern starts or where the pattern ends. You could make a more complicated smudge, but this is at least a reasonable start.
Note: if the most likely source of an attack is from someone reading your smudges, you might as well use 9 dots in your pattern. Your victory lap will quickly defeat them.
Note: if your fingers are oily, it is still possible to tell the order in which the smudges were generated. In this case, your victory lap could simply be a bunch of zig-zags before you let go, as shown in Figure 4 where the red dotted line indicates the zig-zag victory lap.
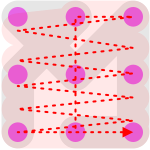
Figure 4. A victory lap forming a zig-zag pattern across the dots.
The first few times, this might annoy you, but you'll get used to it, and pretty soon, it will be habitual.
Note: as a trick, you could have an 8-dot pattern, and then you touch the 9th dot in your zig-zag. Someone watching over your shoulder may only see the first eight dots and then ignore the zig-zags you do to obfuscate the smudges.
Examples of good patterns
Some good patterns are shown in Figure 5. (Good is in italics, because putting them on this page makes them bad patterns—that is, patterns people may immediately try out.
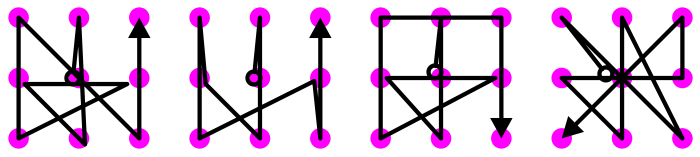
Figure 5. Some good patterns (which, because they are examples here, should not be used).
Mistakes
Unfortunately, there are many mistakes that novices may make that make their patterns much less secure. Make sure you don't do any of these.
Mistake 1. Using 9 dots but only going to neighboring dots and never crossing the line
So many examples online show patterns where the lines don't even cross. Even though you have 9 dots, there are only 400 such patterns. This is less secure than a two letter password, and all possible patterns are shown in Figure 6 up to flips and rotations.
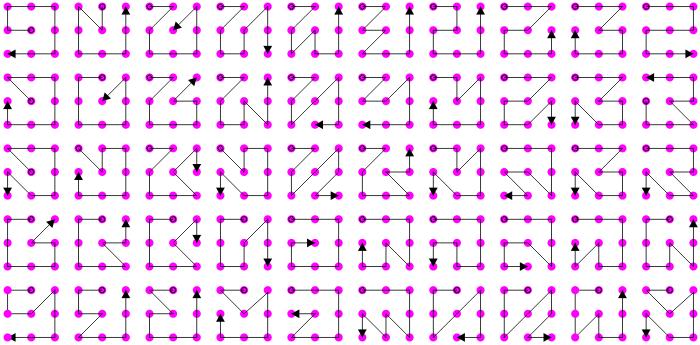
Figure 6. All possible 9-dot patterns without crossing the line.
What I mean by up to flips and rotations is that each pattern actually represents eight different patterns, as shown in Figure 7.
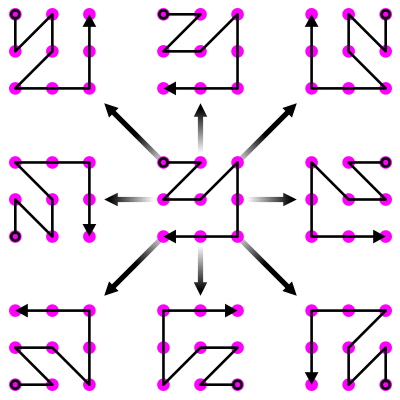
Figure 7. How one pattern represents eight different patterns with flips and rotations.
If you consider all such patterns with 7, 8 or 9 dots (I haven't counted the exact number), this would leave you with about as many patterns as there are two-letter passwords, so this is still not very secure.
Mistake 2. Using 9 dots with line crosses but only going to neighboring dots
If you allow a line cross, but still only visit neighboring dots, as shown in Figure 8, you end up with 784 possible patterns. This is almost twice as good as not crossing any lines, but it is still less than one thousand patterns.
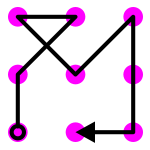
Figure 8. A pattern allowing crossing with 9 dots.
If you consider all possible patterns where you visit 7, 8 or 9 dots (again, allowing you to cross lines but still only visiting adjacent dots), you increase the number of possible patterns to 3568. This is about as secure as a 2.5-letter password.
Note: you may wonder why suddenly we have so many more if we allow 7 or 8 dots. This is because patterns like 1-2-6-9-8-4-5-7 are allowed, as shown in Figure 9.
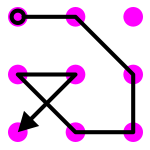
Figure 9. A pattern allowing crossing with 8 dots that cannot be extended to 9 if we restrict ourselves to visiting neighbors only.
Mistake 3. Not doing a victory lap
Even if you have a very complex pattern, the smudges will always make it possible to guess, at the very least, the last two dots in your pattern. In fact, if you consider the pattern in Figure 10, you may think that it is challenging, but a little thought will quickly show that the only way to get this pattern is 6-5-4-2-3-1-9-8-7 or 5-6-4-2-3-1-9-8-7. Now, true, a grade 3 student may not be able to immediately reduce the total number of possibilities to only these two, but the search space is very much reduced.

Figure 10. A smudge from a complex pattern.
Just adding a triangle (from 7, go to 1, 3, and then back to 7) at the end vastly increases the search space, as shown in Figure 11.

Figure 11. A good pattern with a good victory lap.
Mistake 4. Using any of the patterns suggested on this page.
Don't use any example on this page.
The best thing Google could do to make security better
The best thing Google (and the Nexus developers) could do for this is to allow dots to be used multiple times. Many of the weaknesses of the pattern security result from the first constraint (that you can only use each dot at most once). The likelihood of someone forgetting their pattern will be increased, but this could be ameliorated by forcing users of complex patterns to enter their pattern four or five times. Here complex means any pattern that uses a dot more than once. If it is so complex they can't enter it five times in a row, then it's too complex for a secure pattern.



